Author:
john
Posted:
Jun 3, 2024
test blog
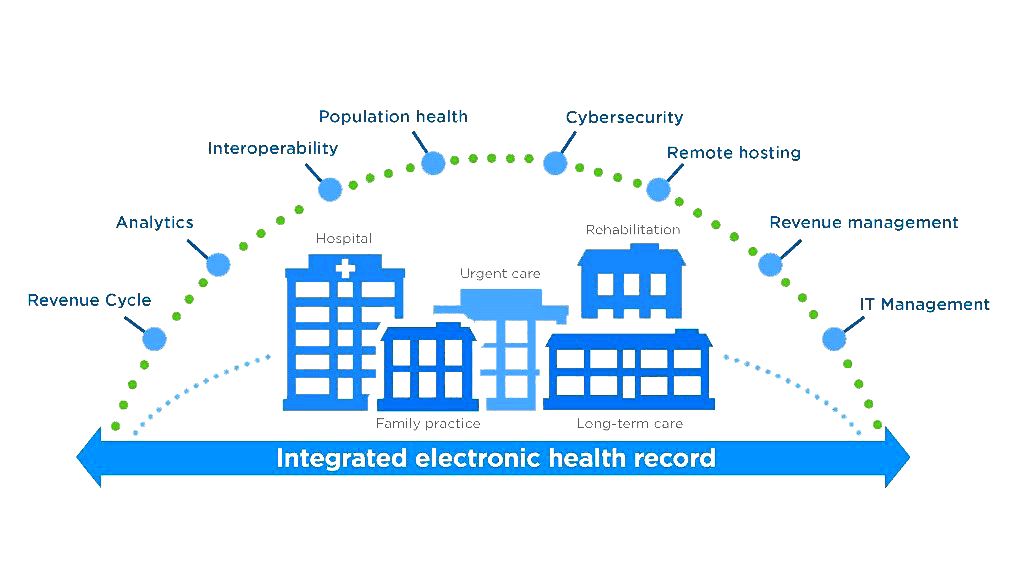

In an era where cyber threats are rapidly evolving and becoming more sophisticated, the integration of cybersecurity best practices into corporate policies and business models has become more crucial than ever. With data breaches and cyber-attacks making headlines, companies are recognizing the need to prioritize cybersecurity not just as a technical issue, but as a strategic business imperative.
The Rising Need for Robust Cybersecurity Strategies:
The increasing reliance on digital technologies has exposed companies to a variety of cyber risks. From protecting sensitive customer data to safeguarding critical infrastructure, the scope of cybersecurity has broadened significantly. This expansion necessitates a holistic approach, integrating robust cybersecurity measures into the very fabric of business operations and policies.
Key Elements Companies Seek in Cybersecurity Vendors:
As companies look to reinforce their cybersecurity defenses, selecting the right cybersecurity vendor becomes pivotal. They typically evaluate several key factors to ensure optimal protection:
Security Needs Assessment: Understanding specific security needs, risk profiles, and regulatory requirements.
Expertise and Reputation: Vendors must have proven expertise and a positive reputation in the cybersecurity field.
Comprehensive Solution Offering: A suite of services covering various cybersecurity aspects is preferred.
Customization and Scalability: Solutions should be tailored to specific needs and scalable as the company grows.
Ease of Integration: Seamless integration with existing IT infrastructure is crucial.
Compliance and Regulatory Requirements: Solutions must comply with relevant industry standards and regulations.
Cost Effectiveness: A balance between cost and value offered by the solutions.
Support and Training: Robust support services and training for staff are essential.
Innovation and Future-Proofing: Solutions should be innovative and adaptable to emerging threats.
Data Privacy and Security Standards: Adherence to stringent security standards is critical.
User-Friendly Interface: Systems should be efficient and easy to use.
Incident Response and Recovery: Quick and efficient handling of security breaches is necessary.
Integrating Cybersecurity into Business Models:
For cybersecurity to be effective, it must be woven into the company’s business model and culture. This involves:
Developing Comprehensive Policies: Cybersecurity policies should be clear, comprehensive, and integrated into all levels of the organization.
Employee Training and Awareness: Regular training and awareness programs for employees are crucial to prevent human error, often the weakest link in cybersecurity.
Risk Management Integration: Cybersecurity should be a part of the overall risk management strategy, with regular assessments and updates.
Incorporating Cybersecurity in Decision Making: Cybersecurity should be part of strategic decisions from product development to mergers and acquisitions.
Regular Audits and Compliance Checks: Ensuring that cybersecurity measures are up-to-date and compliant with regulatory standards.
Explore more blogs


The efficacy of different mobile security approaches.


The efficacy of different mobile security approaches.


The efficacy of different mobile security approaches.
View more
Let’s have a chat!
Let’s have a chat!
Get insights into your web security
Get insights into your web security
Contact us
Subscribe to Our Newsletter
Signup today for free and get notified of the next newsletter updates.
Enter your email address
SUBSCRIBE

CORE draws on decades of industry expertise in Information Security, Cybersecurity, and Risk Management, honed in multinational corporations and auditing, to safeguard your business's critical systems and networks effectively.
Links
Home
About us
Industries
Services
FAQ
Challenge
CSAT
Blog
Latest news
Why Cybersecurity is Essential for Your Business: A Comprehensive Guide
Cybersecurity Essentials: Understanding the Threat Landscape and Protective Measures
Integrating Cybersecurity Best Practices into Corporate Policies and Business Models: A Strategic...
Contact us
03 5789 5744
info@coresecurity.co.jp

CORE draws on decades of industry expertise in Information Security, Cybersecurity, and Risk Management, honed in multinational corporations and auditing, to safeguard your business's critical systems and networks effectively.
Links
Home
About us
Industries
Services
FAQ
Challenge
CSAT
Blog
Latest news
Why Cybersecurity is Essential for Your Business: A Comprehensive Guide
Cybersecurity Essentials: Understanding the Threat Landscape and Protective Measures
Integrating Cybersecurity Best Practices into Corporate Policies and Business Models: A Strategic...
Contact us
03 5789 5744
info@coresecurity.co.jp


Author:
john
Posted:
Jun 3, 2024
test blog


In an era where cyber threats are rapidly evolving and becoming more sophisticated, the integration of cybersecurity best practices into corporate policies and business models has become more crucial than ever. With data breaches and cyber-attacks making headlines, companies are recognizing the need to prioritize cybersecurity not just as a technical issue, but as a strategic business imperative.
The Rising Need for Robust Cybersecurity Strategies:
The increasing reliance on digital technologies has exposed companies to a variety of cyber risks. From protecting sensitive customer data to safeguarding critical infrastructure, the scope of cybersecurity has broadened significantly. This expansion necessitates a holistic approach, integrating robust cybersecurity measures into the very fabric of business operations and policies.
Key Elements Companies Seek in Cybersecurity Vendors:
As companies look to reinforce their cybersecurity defenses, selecting the right cybersecurity vendor becomes pivotal. They typically evaluate several key factors to ensure optimal protection:
Security Needs Assessment: Understanding specific security needs, risk profiles, and regulatory requirements.
Expertise and Reputation: Vendors must have proven expertise and a positive reputation in the cybersecurity field.
Comprehensive Solution Offering: A suite of services covering various cybersecurity aspects is preferred.
Customization and Scalability: Solutions should be tailored to specific needs and scalable as the company grows.
Ease of Integration: Seamless integration with existing IT infrastructure is crucial.
Compliance and Regulatory Requirements: Solutions must comply with relevant industry standards and regulations.
Cost Effectiveness: A balance between cost and value offered by the solutions.
Support and Training: Robust support services and training for staff are essential.
Innovation and Future-Proofing: Solutions should be innovative and adaptable to emerging threats.
Data Privacy and Security Standards: Adherence to stringent security standards is critical.
User-Friendly Interface: Systems should be efficient and easy to use.
Incident Response and Recovery: Quick and efficient handling of security breaches is necessary.
Integrating Cybersecurity into Business Models:
For cybersecurity to be effective, it must be woven into the company’s business model and culture. This involves:
Developing Comprehensive Policies: Cybersecurity policies should be clear, comprehensive, and integrated into all levels of the organization.
Employee Training and Awareness: Regular training and awareness programs for employees are crucial to prevent human error, often the weakest link in cybersecurity.
Risk Management Integration: Cybersecurity should be a part of the overall risk management strategy, with regular assessments and updates.
Incorporating Cybersecurity in Decision Making: Cybersecurity should be part of strategic decisions from product development to mergers and acquisitions.
Regular Audits and Compliance Checks: Ensuring that cybersecurity measures are up-to-date and compliant with regulatory standards.
Explore more blogs


The efficacy of different mobile security approaches.


The efficacy of different mobile security approaches.
View more
Let’s have a chat!
Get insights into your web security
Contact us

CORE draws on decades of industry expertise in Information Security, Cybersecurity, and Risk Management, honed in multinational corporations and auditing, to safeguard your business's critical systems and networks effectively.
Links
Home
About us
Industries
Services
FAQ
Challenge
CSAT
Blog
Latest news
Why Cybersecurity is Essential for Your Business: A Comprehensive Guide
Cybersecurity Essentials: Understanding the Threat Landscape and Protective Measures
Integrating Cybersecurity Best Practices into Corporate Policies and Business Models: A Strategic...
Contact us
03 5789 5744
info@coresecurity.co.jp

CORE draws on decades of industry expertise in Information Security, Cybersecurity, and Risk Management, honed in multinational corporations and auditing, to safeguard your business's critical systems and networks effectively.
Links
Home
About us
Industries
Services
FAQ
Challenge
CSAT
Blog
Latest news
Why Cybersecurity is Essential for Your Business: A Comprehensive Guide
Cybersecurity Essentials: Understanding the Threat Landscape and Protective Measures
Integrating Cybersecurity Best Practices into Corporate Policies and Business Models: A Strategic...
Contact us
03 5789 5744
info@coresecurity.co.jp
Subscribe to Our Newsletter
Signup today for free and get notified of the next newsletter updates.
Enter your email address
SUBSCRIBE