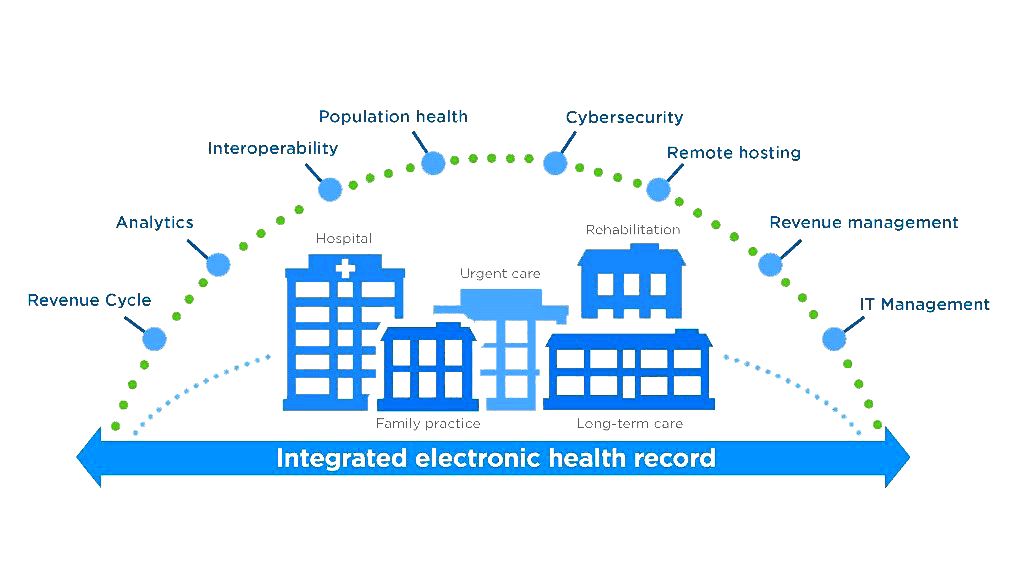
some small description
Healthcare and Life Sciences:
CORE has subject matter experts in financial services (securities, asset management, investment banking, insurance, banking) and healthcare and life sciences (including physicians, hospital owners, and directors). CORE experts understand the industry's details at the cutting edge and are advising clients expertly as their peers on all aspects of governance, operations, regulatory matters, and much more.
Reference Papers
Feel free to download the following papers on cybersecurity in healthcare:
1. Application of Blockchain to Maintaining Patient Records in Electronic Health Record for Enhanced Privacy, Scalability, and Availability Dara Tith, Joong-Sun Lee, Hiroyuki Suzuki, W. M. A. B. Wijesundara, Naoko Taira, Takashi Obi, Nagaaki Ohyama Institute of Innovative Research, Tokyo Institute of Technology, Yokohama, Japan.
2. CIED Cybersecurity Risks in an Increasingly Connected World, Jessica E. Paulsen, BE Matthew B. Hazelett, BS Suzanne, B. Schwartz, MD, 2018 American Heart Association, Inc.
3. Cybersecurity features of digital medical devices: an analysis of FDA product summaries Ariel Dora Stern, 1,2 William J Gordon,3,4 Adam B Landman,3 Daniel B Kramer4,5, Stern AD, et al. BMJ Open 2019;9:e025374. doi:10.1136/bmjopen-2018-025374.
4. Cybersecurity for Cardiac Implantable Electronic Devices, Adrian Baranchuk, MD, a Marwan M. Refaat, MD, Kristen K. Patton, MD, Mina K. Chung, MD,d Kousik Krishnan, MD, Valentina Kutyifa, MD, Ph.D., Gaurav Upadhyay, MD, John D. Fisher, MD, Dhanunjaya R. Lakkireddy, MD, from the American College of Cardiology’s Electrophysiology Section Leadership, J. Amer. Coll. of Cardiology, Vol . 7 1 , No . 1 1 , 2 0 1 8.
5. Cybersecurity and medical devices: A practical guide for cardiac electrophysiologists, Benjamin Ransford Ph.D., Daniel B. KramerMD, MPH, Denis Foo Kune Ph.D., Julio Auto de Medeiros BS, Chen Yan BS, Wenyuan Xu Ph.D., Thomas CrawfordMD, Kevin Fu Ph.D., Pacing Clin. Electrophysiol. 2017;40:913–917.
6. Cybersecurity implications for hospital quality, Christian Dameff MD, Michael A. Pfeffer MD, Christopher A. Longhurst MD, Health Serv Res. 2019;54:969–970.
7. Cybersecurity in healthcare: A systematic review of modern threats and trends, Clemens Scott Kruse, Benjamin Frederick, Taylor Jacobson, and D. Kyle Monticone, Technology and Health Care 25 (2017) 1–10 1 DOI 10.3233/THC-161263.
8. Health IT, hacking, and cybersecurity: national trends in data breaches of protected health information, Jay G. Ronquillo, J. Erik Winterholler, Kamil Cwikla, Raphael Szymanski, and Christopher Levy, JAMIA Open, 1(1), 2018, 15–19 doi: 10.1093/jamiaopen/ooy019.
9. How hospitals can protect themselves from cyber attack, Brian Owens, CMAJ 2020 January 27;192:E101-2. doi: 10.1503/cmaj.1095841
Want to know how to protect your medical practice?
Let’s have a chat!
Get insights into your web security
Contact us
Subscribe to Our Newsletter
Signup today for free and get notified of the next newsletter updates.
Enter your email address
SUBSCRIBE

CORE draws on decades of industry expertise in Information Security, Cybersecurity, and Risk Management, honed in multinational corporations and auditing, to safeguard your business's critical systems and networks effectively.
Links
Home
About us
Industries
Services
FAQ
Challenge
CSAT
Blog
Latest news
Why Cybersecurity is Essential for Your Business: A Comprehensive Guide
Cybersecurity Essentials: Understanding the Threat Landscape and Protective Measures
Integrating Cybersecurity Best Practices into Corporate Policies and Business Models: A Strategic...
Contact us
03 5789 5744
info@coresecurity.co.jp